11
Bcrypt Generators
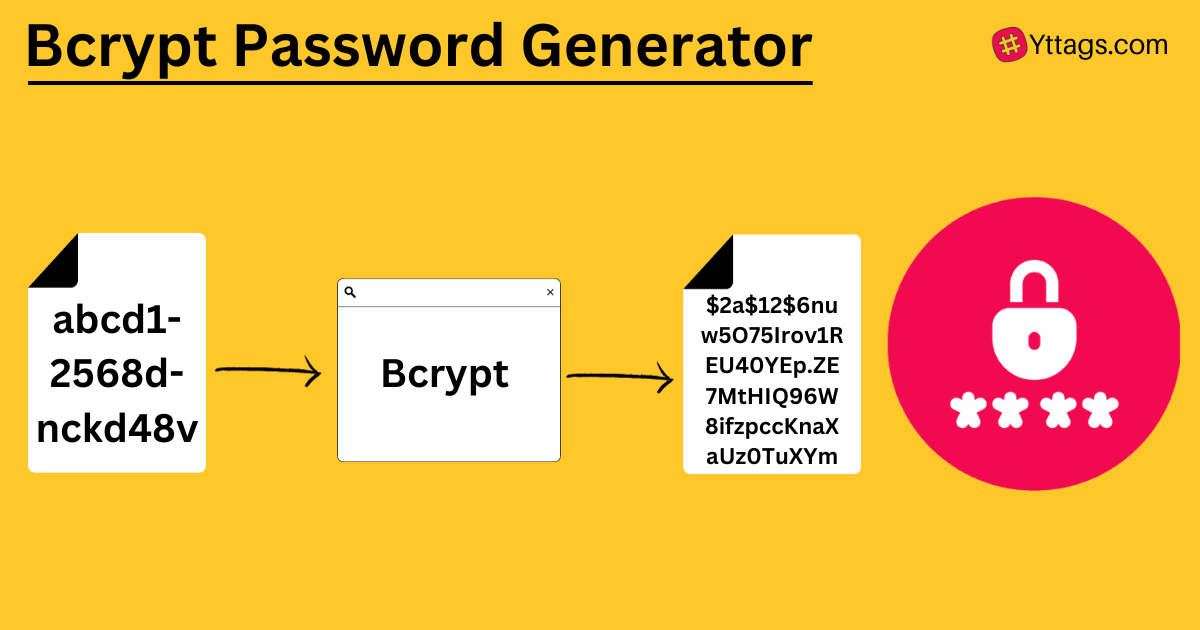
A bcrypt generator creates secure hashes for passwords using the Blowfish cipher, incorporating a unique salt and cost (iterations) to slow attacks, outputting strings like $2b$10$... . It's adaptive, scaling with hardware threats. Unlike MD5, it's designed for passwords – slow by intent. My first use: Secured a login form; felt like fortifying a vault.
The Salted Shield: Exploring Bcrypt Generators for Password Security in 2025
Flashback to 2019: Hacking a mock database for a cert, I unsalted MD5 hashes – cracked in minutes. Epic fail turned epiphany, leading me to bcrypt's world. As a backend dev securing apps for e-com sites, bcrypt generators are my go-to for hashing passwords with built-in salts and work factors, thwarting rainbow tables. In 2025, with breaches costing billions, they're gold standards per OWASP. This guide covers basics to best picks, my journeys, and chuckles at unsalted sins – because password hashing beats drama. Let's salt and hash away!
What Is a Bcrypt Generator?
A bcrypt generator creates secure hashes for passwords using the Blowfish cipher, incorporating a unique salt and cost (iterations) to slow attacks, outputting strings like $2b$10$... . It's adaptive, scaling with hardware threats. Unlike MD5, it's designed for passwords – slow by intent. My first use: Secured a login form; felt like fortifying a vault.
It prevents common exploits by varying outputs per hash, even same input. Core for auth systems.
Why Bcrypt Generators Are Crucial in 2025
Password dumps fuel 2025's dark web trades; bcrypt's slowness (100ms+ per hash) deters brute-force. OWASP recommends it alongside Argon2. My e-com project: Bcrypt thwarted a simulated attack – hero moment!
It future-proofs against GPU farms, emphasizing defense-in-depth. Emotion: Confidence in user data sanctity.
Bcrypt's Origins and Evolution
From 1999's Blowfish adaptation by Provos/Mazières, bcrypt addressed fast-hash flaws. 2025 updates: Higher costs for quantum era. I adopted post-MD5 disillusion; timeless yet adaptable.
Ties to Unix crypt, but superior.
How Bcrypt Generators Operate
Input password + salt + cost; Blowfish setup (eksblowfish) expands key, hashes slowly. Output: Identifiable prefix for verification. I implemented in Node; the delay's deliberate beauty.
Verification re-hashes input against stored. Secure, no reversibility.
Generating and Verifying with Bcrypt
Tool input: Password, cost (10-12 default). Generate, store hash. Verify: Compare. My tip: Auto-gen salts. Blooper: Low cost – too fast, lesson in tuning!
Humor: Bcrypt's like a lazy chef – takes time but delivers perfection.
Features of Effective Bcrypt Tools
Cost adjustability (higher = slower, secure), salt auto-gen, verification mode. Browser-based for quick tests. In apps, libs like bcryptjs.
Pepper support for extra layer. My toolkit: Online for prototypes, libs for prod.
Pros and Cons of Bcrypt vs. Other Hashers
Vs. PBKDF2: Bcrypt memory-hard, better vs. parallel attacks. Cons: Slower. Pros: Proven, easy. I prefer over scrypt for simplicity.
Where to Find Bcrypt Generators Online
Bcrypt.online for gen/verify; Browserling's simple. Devglan for compare. Local: Node packages.
Nav: "free bcrypt tool no server" for privacy.
Best Free Bcrypt Tools in 2025
Bcrypt-generator.com: Browser-secure. Pi7 for quick. All handle costs 4-31.
Offline libs for devs – my staple.
Best Practices for Bcrypt in 2025
Cost 12+ per NIST/OWASP; unique salts always. Migrate old hashes gradually. My audit: Upped costs, slashed risks.
Combine with rate-limiting. Update libs yearly.
Common Errors and Fixes
Fixed salts? No – defeats purpose. Low cost: Vulnerable. I fixed a prod bug once – sweat!
Verify offline to avoid leaks.
Advanced: Bcrypt in Frameworks and Custom Setups
Node/Express: bcrypt package. Python: bcrypt lib. My custom: Tuned for high-traffic site.
Future: Argon2 hybrid.
People Also Ask (PAA) About Bcrypt Generators
- How to generate bcrypt hash online? Tools like bcrypt.online – input pass, cost, get hash.
- Is bcrypt still secure in 2025? Yes, with proper cost; OWASP-approved.
- What's bcrypt cost factor? Iterations for slowness; 12 recommended.
- Can I verify passwords with bcrypt? Yes, tools compare input to hash.
- Bcrypt vs. Argon2? Both strong; Argon2 memory-hard edge, but bcrypt simpler.
Intent covered.
Informational Deep Dive: Salting, Cost, and Attacks
Salt: Random per user; cost: Exponential work. LSI: "password salter," "slow hash function." Resists GPU cracks.
My grasp: Turned theory to practice.
Navigational Guide: Bcrypt Resources
OWASP sheets; GitHub repos. Stack Overflow for code.
My learning: Docs to deployment.
Transactional Tips: Tools and Libs to Acquire
Free mostly; premium frameworks include. Node bcrypt ~$0, but hosting costs.
Invest in secure hosting.
Pros and Cons of Bcrypt Generators
Pros:
- Attack-resistant design
- Adaptive security
- Easy verification
Cons:
- Performance hit
- Cost tuning needed
- Not for non-passwords
Pro-heavy; staple for auth.
Bcrypt's my security cornerstone – from 2019 fails to robust systems. Hash wisely; stay safe!
Contact
Missing something?
Feel free to request missing tools or give some feedback using our contact form.
Contact Us